This is my first write-up. I will try to share something that might help you, and obviously pardon my mistakes.
This blog is all about my reconnaissance of the program, especially the subdomain where I found the vulnerability.
Choosing a Program :)
I never care how many researchers are already working there; I make up my mind that I am the first guy to submit at least one vulnerability. Never be upset that you got a private invitation, and why are so many researchers there?
But ask yourself, if there are numerous researchers, does that mean this program is so buggy or vulnerable? That is the type of motivation you should have.I am not motivated enough.
Instead of being upset, carefully read the program scopes and descriptions to see what they accept and what they do not!
Imagine the program name is “hackerboy.com”
Starting Test :D
Whenever I go for a test a new program, I always start with Sub-domain Enumeration
“knockpy hackerboy.com”“python sublist3r.py -u hackerboy.com”“aquatone”“webscreenshot”
I think these are enough for sub-domain enumerating!
After sub-domain’s info gathered, I chose few sub and tried for some known vulnerabilities, but I could not succeed. I went to google, github, censys, shodan for gathering more info, but I didn’t find anything special.
After one day, while checking all screenshots again, one screenshot took my attention :|
The screenshot was about a sub-domain, which is like fullapi.hackerboy.com
When I visit, I saw some error
All we love to go to find something on “/admin” login page, huh? Don’t we? ✌️
Then I went to “fullapi.hackerboy.com/admin” and I saw an interesting response 😛
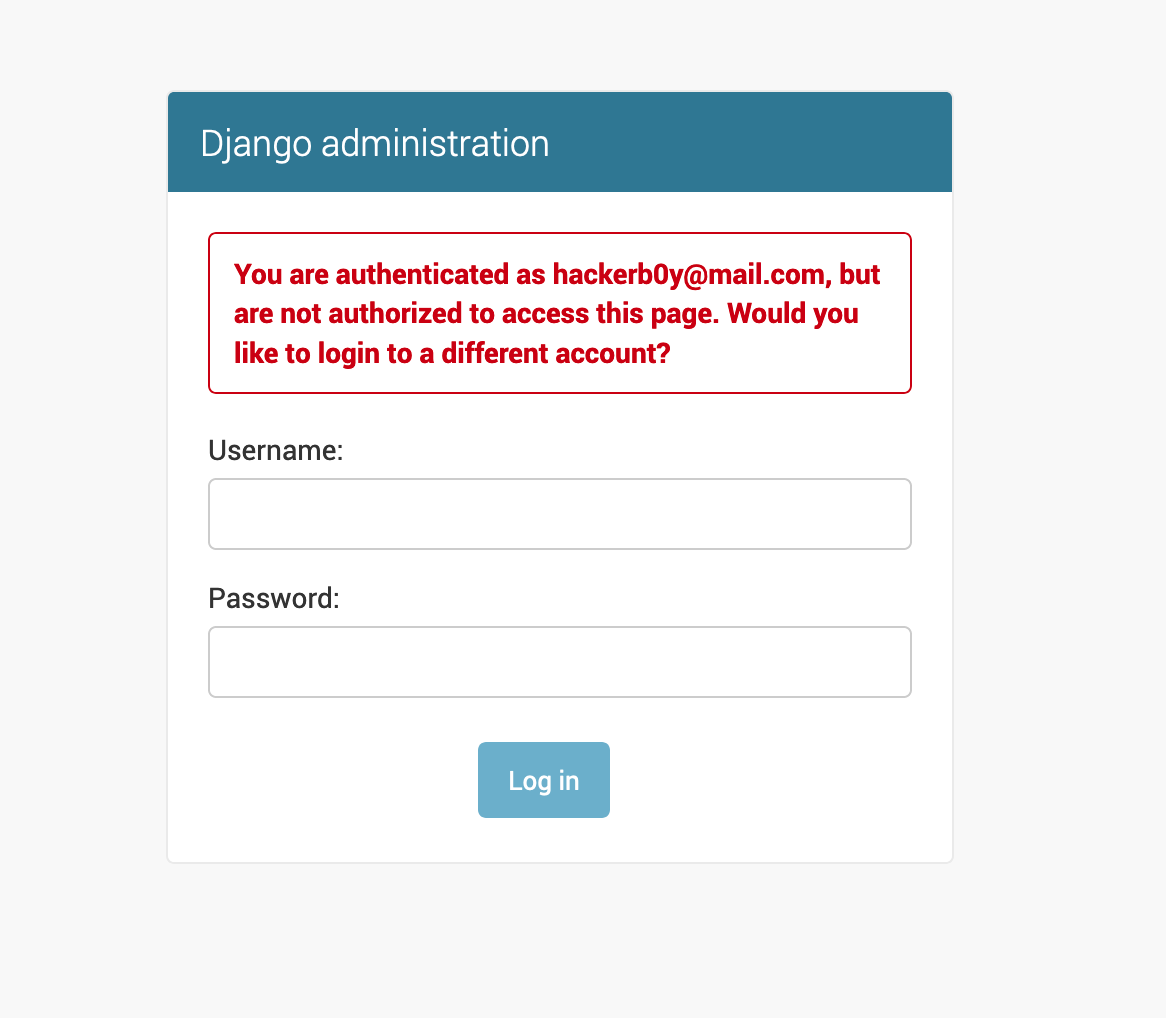
Wait, authenticated? :/
At a glance, I tried with some brute-force attack but didn’t success. Then I did a dirsearch. Then suddenly, I thought Path are already exposing, why should I go for dirsearch? :/
Then I started trying with every path that are exposing. I have visited “fullapi.hackerone.com/account_mngr” and saw this 😵
I click on the “Log in” button, in the right top corner. and I went to a Login Page.
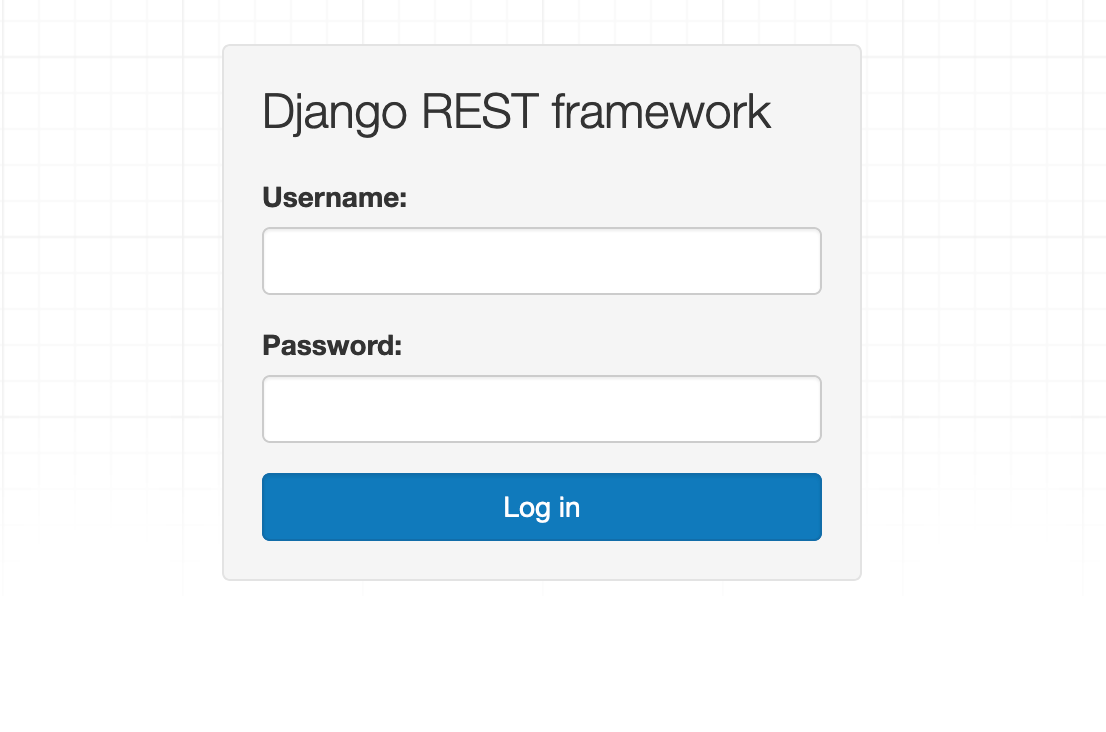
Here comes most significant part of this write-up.
How I bypassed it ? How I logged into this Admin Panel ?
account.hackerboy.com is for all users. Meanwhile, you can create an account and login there! But fullapi.hackerboy.com doesn’t have any registration option either normal users can not login without hackerboy.com’s staffs or employee. Because it’s an “admin panel”.
What I did here is I have created an account on “account.hackerboy.com” and I entered the same login info on “fullapi.hackerboy.com” and guess what ? The server let me logged into the Admin Panel. ^_^
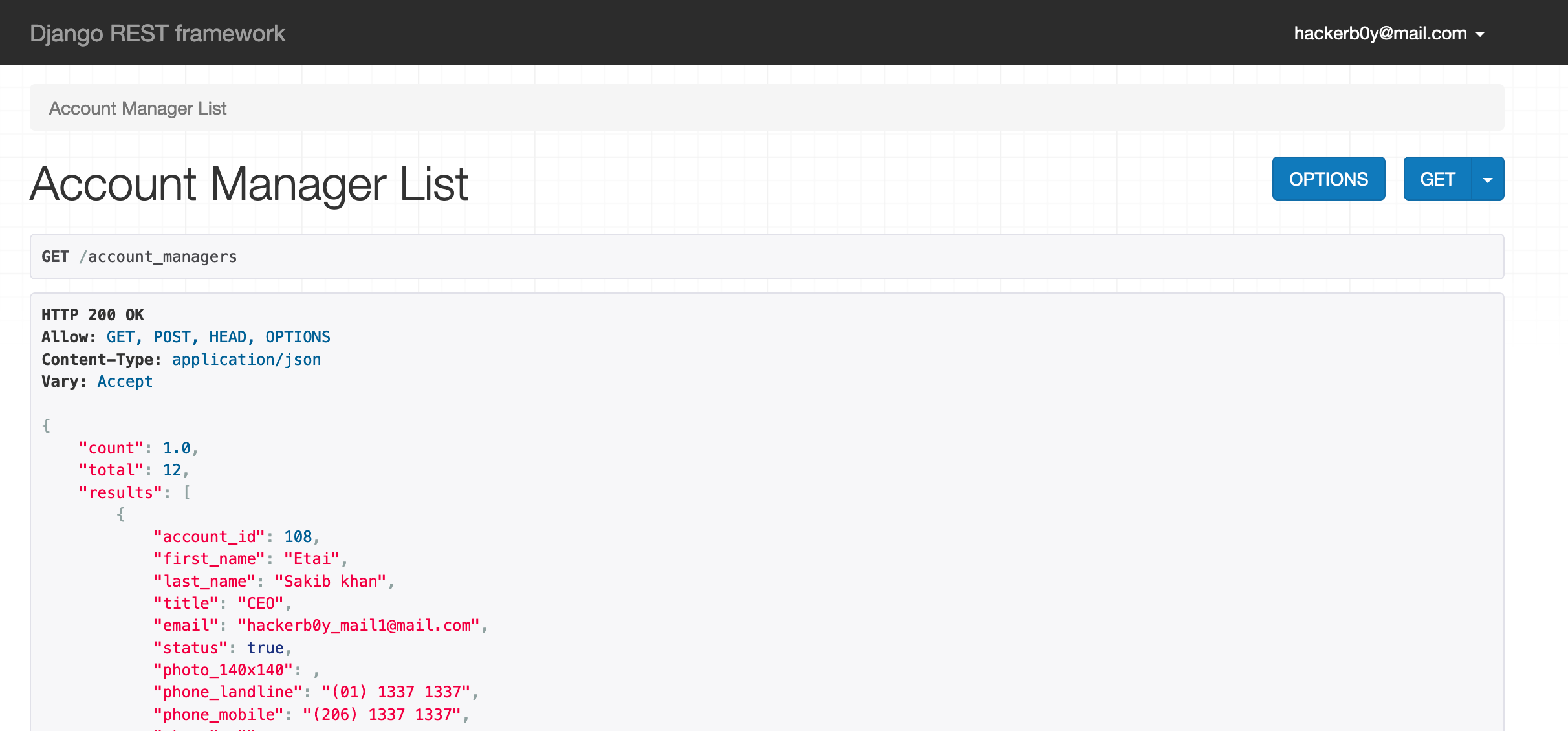 |
| Admin Panel |
w00t? Phone number and other credentials of CEO? 😮
I was thinking that time, why the server let me logged into this panel ? :/ Then suddenly I thought maybe the role of users doesn’t set properly or the server checks only the user is valid or not, if the user account is valid the server let logged anyone into the panel.
One more thing is I think by having authentication misconfiguration anyone can login with user’s registered info! I might me wrong!!!
What can I do with this Admin Panel ?
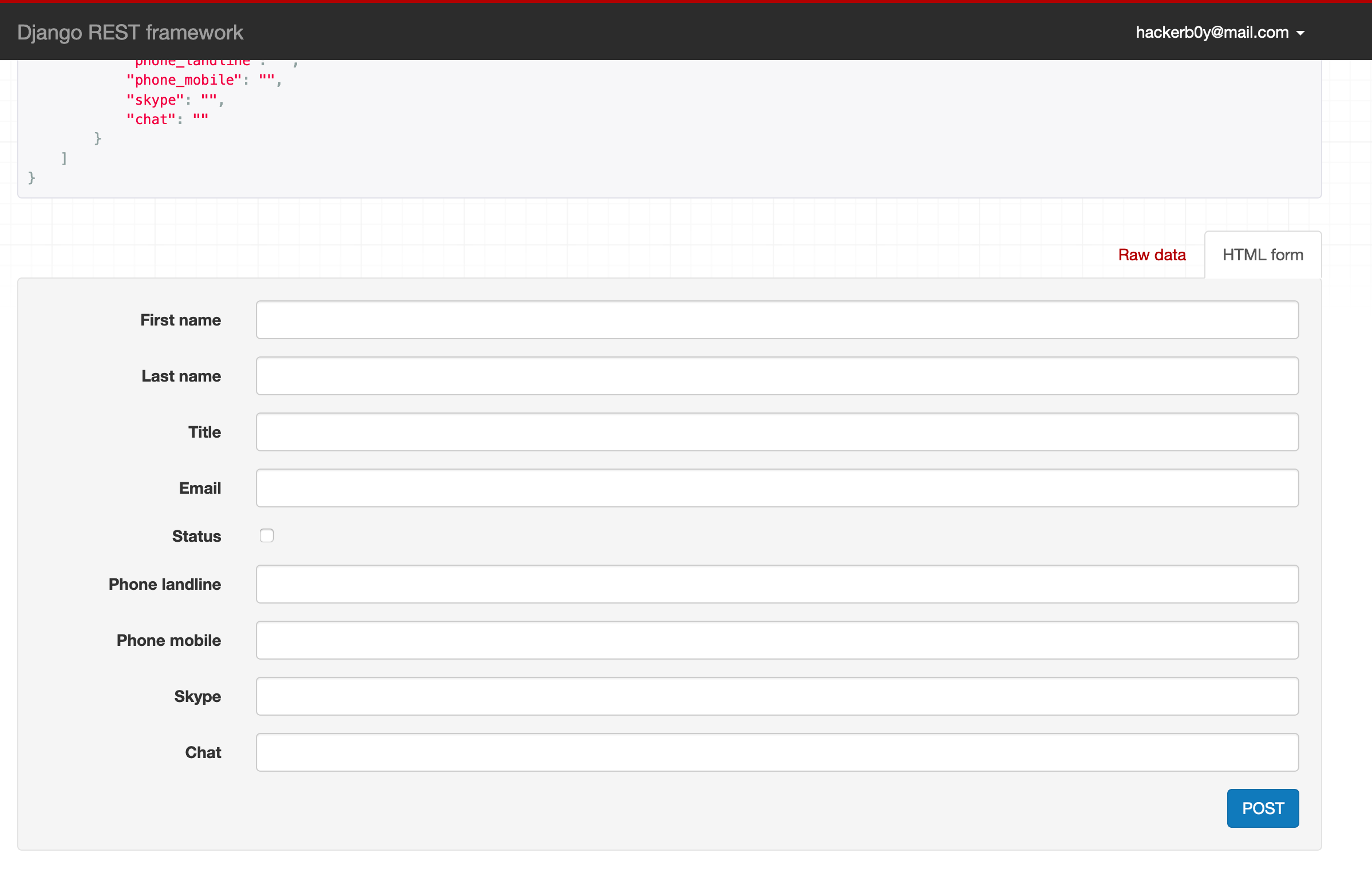
Bounty?
Report triaged on HackerOne, don’t know about the bounty yet. You can ask me anything on my Facebook or Twitter regarding #infosec #bugbounty I will try to help.
Thanks for your valuable time to read it. ^_^


2 Comments
Cool bruh
ReplyDeleteHow much did you owe?
ReplyDeleteThat you got this subdomain fullapi.hackerboy.com only with sublist3r?
Post a Comment